– na vygenerování certifikátu byl použit Centos6
– Let’s Encrypt klient je https://github.com/Neilpang/acme.sh
– pro požadovanou doménu je nutné přidat TXT záznam, takže je nutný přístup do DNS
Stažení klienta
root@emg ~ # curl https://get.acme.sh | sh
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
100 705 100 705 0 0 835 0 --:--:-- --:--:-- --:--:-- 5778
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
100 139k 100 139k 0 0 173k 0 --:--:-- --:--:-- --:--:-- 344k
[Sun Apr 16 17:20:55 CEST 2017] Installing from online archive.
[Sun Apr 16 17:20:55 CEST 2017] Downloading https://github.com/Neilpang/acme.sh/archive/master.tar.gz
[Sun Apr 16 17:20:57 CEST 2017] Extracting master.tar.gz
[Sun Apr 16 17:20:57 CEST 2017] Installing to /root/.acme.sh
[Sun Apr 16 17:20:57 CEST 2017] Installed to /root/.acme.sh/acme.sh
[Sun Apr 16 17:20:57 CEST 2017] Installing alias to '/root/.bashrc'
[Sun Apr 16 17:20:58 CEST 2017] OK, Close and reopen your terminal to start using acme.sh
[Sun Apr 16 17:20:58 CEST 2017] Installing alias to '/root/.cshrc'
[Sun Apr 16 17:20:58 CEST 2017] Installing alias to '/root/.tcshrc'
[Sun Apr 16 17:20:58 CEST 2017] Installing cron job
[Sun Apr 16 17:20:59 CEST 2017] Good, bash is found, so change the shebang to use bash as preferred.
[Sun Apr 16 17:21:00 CEST 2017] OK
[Sun Apr 16 17:21:00 CEST 2017] Install success!
root@emg ~ #
Vygenerování certifikátu
root@emg ~ # cd .acme.sh/
root@emg .acme.sh # ll
total 160
-rw-r--r--. 1 root root 96 Apr 16 17:20 account.conf
-rwxr-xr-x. 1 root root 142525 Apr 16 17:20 acme.sh
-rw-r--r--. 1 root root 78 Apr 16 17:20 acme.sh.csh
-rw-r--r--. 1 root root 78 Apr 16 17:20 acme.sh.env
drwxr-xr-x. 2 root root 4096 Apr 16 17:21 deploy
drwxr-xr-x. 2 root root 4096 Apr 16 17:21 dnsapi
root@emg .acme.sh #
root@emg .acme.sh # ./acme.sh --issue --dns -d intra.strachota.net
[Sun Apr 16 17:23:33 CEST 2017] Registering account
[Sun Apr 16 17:23:36 CEST 2017] Registered
[Sun Apr 16 17:23:38 CEST 2017] Update success.
[Sun Apr 16 17:23:39 CEST 2017] ACCOUNT_THUMBPRINT='9qB5HKEYhoWER4SjfxBO6p1N-cuAn4ApejodRT5Bwx8'
[Sun Apr 16 17:23:39 CEST 2017] Creating domain key
[Sun Apr 16 17:23:39 CEST 2017] Single domain='intra.strachota.net'
[Sun Apr 16 17:23:40 CEST 2017] Getting domain auth token for each domain
[Sun Apr 16 17:23:40 CEST 2017] Getting webroot for domain='intra.strachota.net'
[Sun Apr 16 17:23:40 CEST 2017] Getting new-authz for domain='intra.strachota.net'
[Sun Apr 16 17:23:42 CEST 2017] The new-authz request is ok.
[Sun Apr 16 17:23:43 CEST 2017] Add the following TXT record:
[Sun Apr 16 17:23:43 CEST 2017] Domain: '_acme-challenge.intra.strachota.net'
[Sun Apr 16 17:23:43 CEST 2017] TXT value: 'hdxoUJ50NcB53SdxoKky21jEvqa6tmLrKrEvhRGU-qo'
[Sun Apr 16 17:23:43 CEST 2017] Please be aware that you prepend _acme-challenge. before your domain
[Sun Apr 16 17:23:43 CEST 2017] so the resulting subdomain will be: _acme-challenge.intra.strachota.net
[Sun Apr 16 17:23:43 CEST 2017] Please add the TXT records to the domains, and retry again.
[Sun Apr 16 17:23:43 CEST 2017] Please add '--debug' or '--log' to check more details.
[Sun Apr 16 17:23:43 CEST 2017] See: https://github.com/Neilpang/acme.sh/wiki/How-to-debug-acme.sh
root@emg .acme.sh #
Vygenerování se nepodařilo, protože TXT záznam pro požadovanou doménu neexistuje.
Pro doménu _acme-challenge.intra.strachota.net přidat TXT záznam hdxoUJ50NcB53SdxoKky21jEvqa6tmLrKrEvhRGU-qo
Ověření správnosti DNS
root@emg .acme.sh # nslookup -q=txt _acme-challenge.intra.strachota.net 8.8.8.8|grep text
_acme-challenge.intra.strachota.net text = "hdxoUJ50NcB53SdxoKky21jEvqa6tmLrKrEvhRGU-qo"
root@emg ~ #
Přegenerování certifikátu
root@emg .acme.sh # ./acme.sh --renew -d intra.strachota.net
[Sun Apr 16 19:59:40 CEST 2017] Renew: 'intra.strachota.net'
[Sun Apr 16 19:59:41 CEST 2017] Single domain='intra.strachota.net'
[Sun Apr 16 19:59:41 CEST 2017] Getting domain auth token for each domain
[Sun Apr 16 19:59:42 CEST 2017] Verifying:intra.strachota.net
[Sun Apr 16 20:00:03 CEST 2017] Success
[Sun Apr 16 20:00:03 CEST 2017] Verify finished, start to sign.
[Sun Apr 16 20:00:09 CEST 2017] Cert success.
-----BEGIN CERTIFICATE-----
****************************************************************
****************************************************************
****************************************************************
****************************************************************
****************************************************************
****************************************************************
****************************************************************
****************************************************************
****************************************************************
****************************************************************
****************************************************************
****************************************************************
****************************************************************
****************************************************************
*************************************************************==
-----END CERTIFICATE-----
[Sun Apr 16 20:00:09 CEST 2017] Your cert is in /root/.acme.sh/intra.strachota.net/intra.strachota.net.cer
[Sun Apr 16 20:00:09 CEST 2017] Your cert key is in /root/.acme.sh/intra.strachota.net/intra.strachota.net.key
[Sun Apr 16 20:00:12 CEST 2017] The intermediate CA cert is in /root/.acme.sh/intra.strachota.net/ca.cer
[Sun Apr 16 20:00:12 CEST 2017] And the full chain certs is there: /root/.acme.sh/intra.strachota.net/fullchain.cer
root@emg .acme.sh #
Upload souborů certifikátů do Mikrotiku
root@emg .acme.sh # scp /root/.acme.sh/intra.strachota.net/ca.cer admin@router:/
ca.cer 100% 1647 1.6KB/s 00:00
root@emg .acme.sh # scp /root/.acme.sh/intra.strachota.net/intra.strachota.net.key admin@router:/
intra.strachota.net.key 100% 1679 1.6KB/s 00:00
root@emg .acme.sh # scp /root/.acme.sh/intra.strachota.net/intra.strachota.net.cer admin@router:/
intra.strachota.net.cer 100% 1809 1.8KB/s 00:00
root@emg .acme.sh #
[admin@MikroTik] > file print where type=".key file" or type=".cer file"
# NAME TYPE SIZE CREATION-TIME
0 intra.strachota.net.key .key file 1679 apr/17/2017 22:19:27
1 intra.strachota.net.cer .cer file 1809 apr/17/2017 22:19:33
2 ca.cer .cer file 1647 apr/17/2017 22:19:06
[admin@MikroTik] >
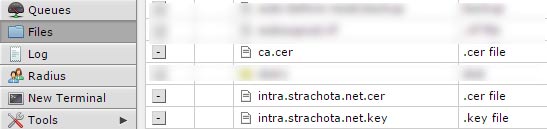
Import certifikátů
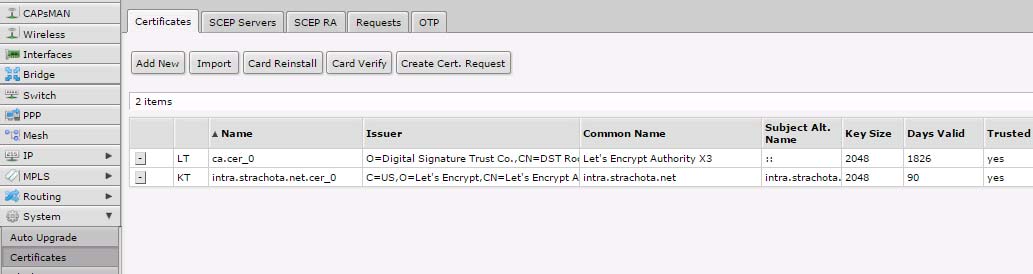
Nastaveni SSL
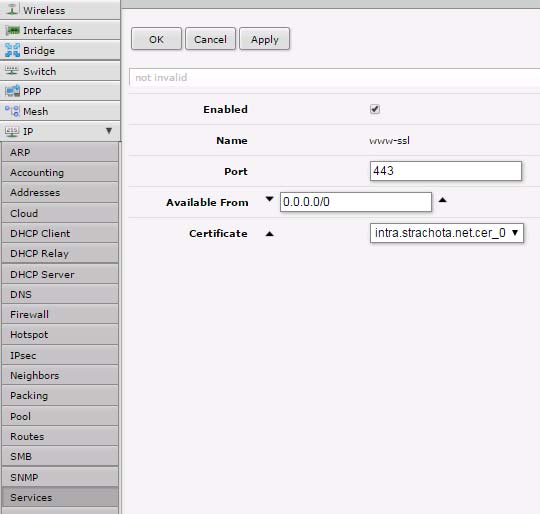
Otevření 443/tcp

Hotovo
Oveření
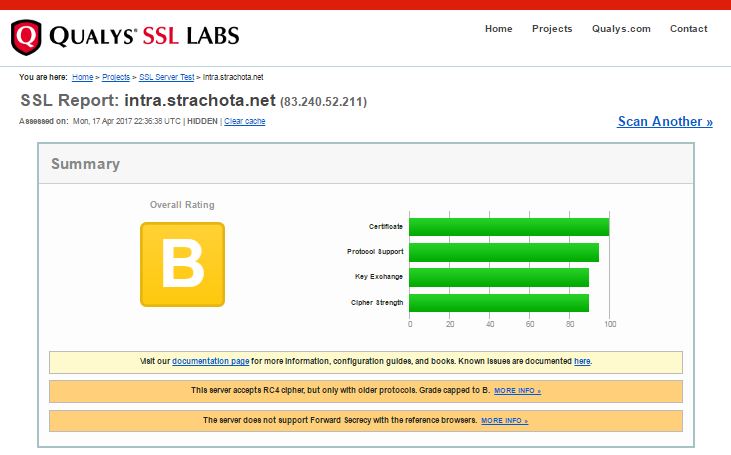
Pomocí ssllabs.com lze zjistit, jak je na tom Mikrotik s konfigurací SSL. Na verzi RouterOS 6.38.5 (duben 2017) dostávám hodnocení „B“, protože akceptuje RC4 a nepodporuje bezpečné generování per session klíče (forward secrecy).